Your cybersecurity program is supposed to protect your organization against today’s dangerous threats, including phishing, ransomware, and data breaches. But simply having a cybersecurity program is not enough. Just like an airplane can’t be considered airworthy unless its engines work flawlessly, your cybersecurity program won’t keep you safe unless you avoid making these common mistakes.
Table of Contents
Keep Your Cybersecurity Program Safe: Avoid Making the Following Common Mistakes
1. Getting Lulled into a False Sense of Security
Your organization isn’t too small to get in the crosshairs of threat actors.
In fact, the chance of you becoming the next target of an opportunistic cybercriminal has never been greater because the number of attacks on SMBs grew from 6,300 attacks per day over the course of 2019 to 31,000 for the year 2021.
This alarming statistic underlines the importance of avoiding making common cybersecurity mistakes; the biggest mistake you could make would be getting lulled into a false sense of security.
Yes, you are a small fish in a big pond, but that doesn’t make you any less tasty.
Cybercriminals can easily target a lot of poorly protected SMBs to benefit financially.
2. Relying on Passwords Alone
It’s estimated that around 80 percent of data breaches are the result of poor or reused passwords.
Still, many organizations continue to rely on passwords alone when it comes to authentication even though much more robust alternatives have been available for ages.
Multi-factor authentication (MFA), the use of one or more additional authentication factors, can prevent 99.99 percent of attacks on your accounts.

Passwordless authentication can achieve similarly fantastic results while making employees’ lives easier by eliminating the password prompt.
3. Using Outdated Software
Would you feel safe at home if you knew that the lock on your front door has a fatal design flaw that allows anyone to open it using readily available tools?
You wouldn’t, of course. But if you’re using outdated software, then it’s likely that your network is just as vulnerable.
According to one survey of IT professionals, one in three breaches are caused by unpatched vulnerabilities – such as the now infamous Log4j vulnerability.

The solution is simple: patch everything and patch often. The potential downtime caused by patching is nothing compared with the potential downtime following a data breach.
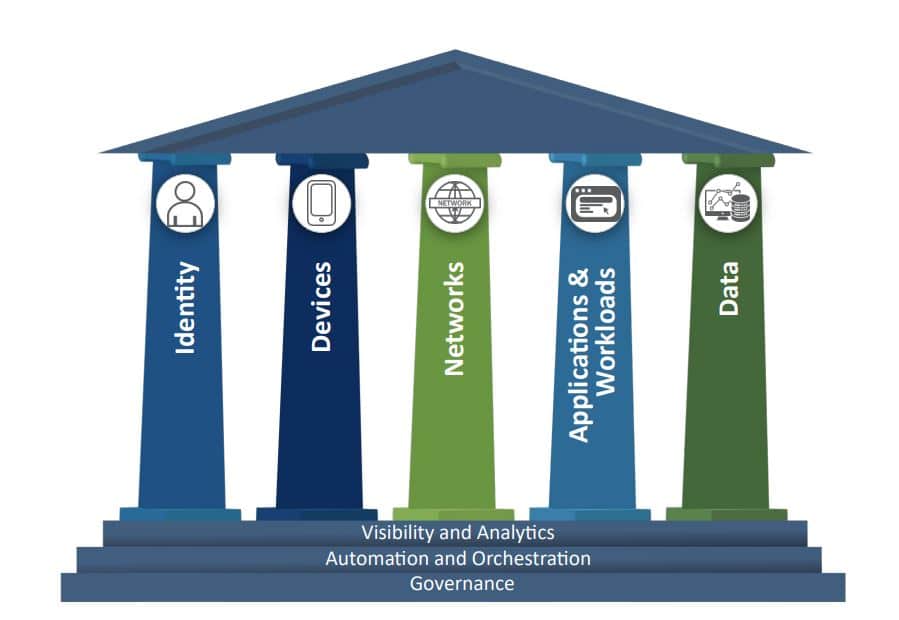
4. Focusing on the Network Perimeter
Back when business owners first started hearing and talking about digital transformation, there was no cloud, no smartphones, and laptops weighed more than some bicycles.
With most SMBs using not much more than a small handful of desktop computers and perhaps one or two in-house servers, it made sense to build a digital wall around the compact network perimeter.
But times have changed, and the network perimeter has become blurred beyond recognition. Traditional firewalls and antivirus software no longer effectively protect data in the cloud or devices used by remote employees.
Instead of continuing to focus on what remains of the network perimeter, SMBs should be moving toward zero trust security, a security model that doesn’t trust any user, device, or application by default.
5. Not Sufficiently Training Employees
You can turn your organization into a small fortress to keep today’s digital threats at bay, but all your effort can quickly go to waste if you make the mistake of not sufficiently training your employees to recognize and respond to the threats you fear so much.
When employees lack basic cybersecurity awareness, they may unknowingly let cybercriminals in by falling for phishing scams, downloading infected attachments, or sharing their login details.
Regular cybersecurity awareness training sessions can make this scenario far less likely to happen.

Learn how to implement an engaging and successful cybersecurity awareness training program.
Bonus: Neglecting Data Backup
Cyber attacks are inevitable, but their consequences are manageable.
A robust cybersecurity program should be able to shield your organization from even the most sophisticated threats, but no defenses will ever be 100 percent impenetrable, so neglecting data backup is one of the worst mistakes you can make.
By backing up all important data—both local and cloud—you gain the ability to quickly recover from any cybersecurity incident.
The sooner you’re back on your feet, the sooner you can go back to what you do best: delivering great products and services to your customers.
Losing access to critical business data can bring your operations to a costly standstill. But by implementing a proven backup framework, you ensure you can recover quickly and minimize costly downtime. Prepare for everything from cyberattacks to natural disasters now.
Avoid Making Costly Cybersecurity Mistakes
These cybersecurity mistakes and others can have disastrous consequences. Cybersecurity experts at Teal can help you avoid them.
Contact us today to discuss how we can take your cybersecurity program to the next level.














