Identity crimes, like other cybercrime activities, are always changing and adapting. Internet access provides easy access to potential victims at an inexpensive cost to cybercriminals. Unfortunately, people do not take the time to learn how to safeguard their identities and presence. And it shows. So, let’s look at how to protect your identity online with 11 best practices!
Table of Contents
Why Protecting Your Identity Online is Important
As your business grows, so does your risk profile.
Cybercriminals aren’t just looking to disrupt operations. They’re after your money, data, and reputation. And they’ll use any method available to get what they want, including:
Scamming your team out of money through phishing or social engineering.
Fraudulently filing tax returns using your business’s information.
Stealing your contact lists and selling them on the dark web.
Opening credit cards or securing loans in your company’s name.
Harvesting and selling sensitive client or vendor data.
Gaining unauthorized access to your business bank accounts.

Key Facts about Identity Theft & Cyber Crime
The Small Business Innovation Research (SBIR) reported that small businesses “remain susceptible to cyber attacks due to lack of resources and surprisingly, a lack of knowledge of the threat .”
The National Cybersecurity Institute noted that 50 percent of SMBs have been a victim of cyber attacks. Worse yet, over 60 percent of them went out of business (LeClair, 2015).
According to Accenture, the insurance industry was the largest target for ransomware attacks in the first half of 2021. Ransomware accounted for almost 25 percent of attacks on their clients.
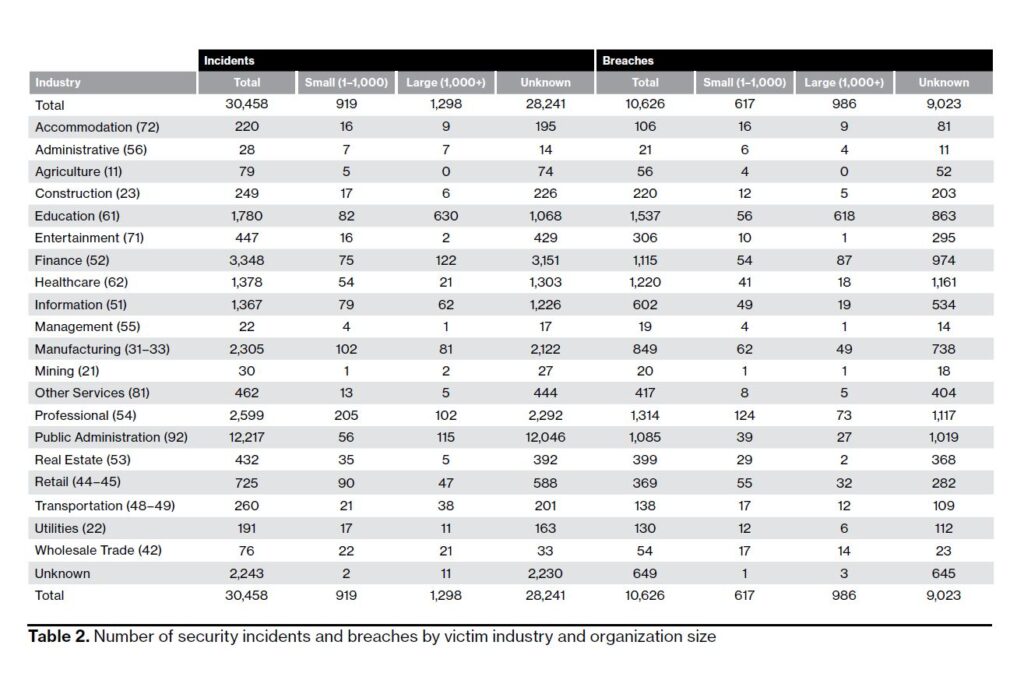
The U.S. Federal Trade Commission (FTC) reported that consumers lost more than $5.8 billion to fraud in 2021. This is a whopping 70 percent increase over the previous year.
FTC’s Consumer Sentinel Network took in over 5.7 million reports in 2021. Of those reports, 49% were for fraud and 25% were for identity theft.
Of the 2.8 million consumers (about the population of Mississippi) who reported to the Consumer Sentinel Network, the most common category was imposter scams. Together, they scammed them out of $2.3 billion. Online shopping scams trailed a bit further behind. Yet, this still cost consumers an incredible $392 million.
Digital Fraud: How Scammers Reach You
Fraudsters don’t discriminate. They will take money and information from anyone, and they’ll get to you no matter how you choose to use technology.
They’ll find you through:
- Online Ads or Pop-ups
- Websites
- Apps
- Emails
- Social Media
- Texts/Phone Calls
A great example of a social media scam is when scammers used Twitter’s (now X’s) new blue check feature to manipulate people. The social platform’s rush to launch the new Twitter Blue subscription led to chaos. The best way to stop scams like these is to learn what it looks like and implementing best practices.
Let’s look at a few examples of digital identity theft. Plus, the ways you can safeguard your personal identity data and online presence.
Business Identity Theft
Business identity theft occurs when someone creates, uses, or tries to use identifying information of a business. Cybercriminals file fraudulent business returns to receive refundable business credits. They also use it to extend individual identity theft.
For example, a Machine-in-the-Middle (MitM) attack on unsecured networks (like public Wi-Fi) can intercept sensitive business data. This gives cybercriminals the access they need to impersonate your company, file fraudulent tax returns, or extend identity theft to individuals tied to your organization.
Many potential red flags could be filing or processing errors. These make business identity theft more complicated than individual identity theft.
How to Know You Are a Victim of Business Identity Theft
- You see a new line of credit or other accounts opened on your credit report you didn’t authorize.
- You receive bills for business credit/credit cards you did not take out.
- You notice unexplained bank account withdrawals.
- You stop receiving bills and other mail items.
- You receive a notification that information was compromised by a data breach with a company you do business with or have an account with.
Discover how to prevent a data breach within your small business or what actions you should take if your business information has been compromised from the IRS.
Digital Business Risk: E-Skimming
In 2019, the FBI shared insights into e-skimming. Their message targeted SMBs and government agencies. They warned that if you take credit card payments online, then you may become a victim of e-skimming.
This online scam involves cybercriminals putting malicious code onto your website. It allows them to capture your credit card data in real-time.
They do this after gaining access to your server. Either through a phishing attack or via a third-party vendor attached to your server.
How to Protect Your Business from E-skimming
- Ensure your antivirus and anti-malware are up to date.
- Change default login credentials on all systems.
- Educate your staff with security awareness training (e.g., never click on links or unexpected attachments in messages).
- Segregate and segment network systems. Limit cybercriminals’ access from one to another.

Learn how to implement an engaging and successful cybersecurity awareness training program.
Medical Identity Theft
Medical identity theft is a massive risk in the healthcare industry. During a data breach, someone gains access to sensitive data. They get your Protected Health Information (PHI) from an insurance company or healthcare provider.
Stolen health information is 20 to 50 times more valuable on the black market than other types of identity fraud.
They can then:
- Sell the information (on the Dark Web your PHI is worth $250 to $1000)
- Bill for made-up medical services (e.g., a medical provider uses patient health info to submit misleading claims for financial benefits)
- Receive free healthcare by sending fraudulent claims to health insurers without your authorization

Download a free copy of your guide today to learn about the Dark Web and how to protect your small business.
Financial Identity Theft
Financial identity theft occurs when a person uses someone else’s personal data for financial gain. It is the most common form of identity theft.
A scammer might:
- Open new accounts using your personal identifying information.
- Use your credit card information to make purchases.
- Steal money out of your bank accounts.
The best way to combat this is through due diligence. Watch all accounts for unexplained charges. If you find one, immediately report it to your bank or credit card company. It is also important to watch your credit report for new accounts or a decrease in score.

11 Ways to Protect Your Identity Online
1. Beware of Public Wi-Fi
Public Wi-Fi isn’t secure. Yet, there are ways to safeguard your information when you are on the go. Implement best practices such as:
- Choose to not access personal of financial information on public Wi-Fi.
- Don’t stay permanently logged into websites.
- Consider using a virtual private network (VPN). Many VPNs offer data encryption that will help secure your information.
- Utilize your mobile data. Mobile data is usually encrypted.
- Listen to warnings from your web browsers. They will often alert you before you enter a fraudulent site or download malicious programs.
- Install browser plug-ins that force your browser to use encryption on popular websites that aren’t encrypted.
- Turn off your device’s setting that automatically connects to nearby Wi-Fi.

Data doesn’t just sit in an office anymore. It travels with us. Equip your team with this checklist of 19 essential practices to safeguard business data while on the go.
2. Build Strong Passwords
Weak passwords make data breaches easy. NordPass published a report that found employees at Fortune 500 companies were using passwords that were easily hacked in less than a second.

Strong passwords are the foundation of your business’s cybersecurity strategy. Without them, your organization could be vulnerable to costly breaches and cyberattacks. Add these best practices to your password policy.
Unfortunately, most people aren’t using strong passwords—and even worse, they’re reusing the same ones across multiple accounts.
3. Always Use MFA
MFA stands for multi-factor authentication. It is an authentication method that requires the user to provide two or more verification factors to gain access to a resource.
It is a core component of a strong identity and access management (IAM) policy. If you have the choice, use it to decrease the likelihood of a successful cyber attack.
4. Scan Email Links & Attachments
Be especially cautious when you receive an unexpected email. Make sure to always hover your cursor over links to verify that the link is from a trusted site.

Strengthen your organization’s defenses against advanced cyberattacks, like ransomware, by elevating phishing awareness with these expert tips and actionable insights.
5. Limit Social Sharing
Cybercriminals love social media because people often overshare personal information. They can piece data from social sites together to conduct identity theft or conduct cyber attacks.
Make an informed decision before posting info on your profile. Use privacy settings to prevent your data from being easily accessible.
6. Note a Website's Security
Secure websites feature “https” at the beginning of the web address. These sites encrypt data. This helps keep your personal data safe.
However, scammers know how to create these encrypted sites too. They often create fake, encrypted sites that look like organizations you are familiar with. This means that not all https sites are legit.
The internet is full of hidden threats because cybercriminals are always looking for ways to exploit businesses. Without proper browsing security, your organization could be vulnerable to malware, phishing, and data breaches. Implement safe browsing practices today to reduce your risk.
A truly secure, legitimate site should:
- Feature a modern, up-to-date design.
- Have a correctly spelled URL (website address) with no typos or lookalike characters.
- Display security seals that link to the issuing company’s website for more details.
- Avoid spamming you with exaggerated promises, unusually low prices, or blinking ads.
7. Regularly Install Updates & Patches
Installing updates and security patches might not be fun, but it is important to your cybersecurity. Uninstalled patches can leave you vulnerable to cyber attacks. You’re leaving the door open for cybercriminals to steal your personal data.
8. Look Out for Signs of Scamming
Watch for these signs to identify an online scam attempt:
- You’re unexpectedly contacted.
- You’re told to keep a transaction a secret.
- The message requires urgent action.
- You’re asked to wire money or to buy prepaid debit cards.
- You’re asked to supply personal information.
- The message you receive sounds too good to be true.
9. Secure Data with Backups
Data security is an essential aspect of your business continuity. Data backups are an important part of this process because it allows you to have a copy of your systems ready to restore. Encrypt the backup file for added security.
Losing access to critical business data can bring your operations to a costly standstill. But by implementing a proven backup framework, you ensure you can recover quickly and minimize costly downtime. Prepare for everything from cyberattacks to natural disasters now.
10. Be Wary of Unexpected Texts & Phone Calls
One of your business’s key vendors is calling. You answer, only to learn that a payment for services—now overdue by months—is urgently needed. Your company owes them $5,238.21.
They warn that they’ll end their contract if you don’t pay today. To complicate matters, you’re responsible for handling their payments.
How did this happen? You’re busy, under pressure from the executive team, and things have been tough at home. The call ends, but soon after, the vendor texts, demanding payment within the hour, threatening to work with a competitor if they don’t receive it. Panic sets in.
You can’t afford to lose your job. Resolving this immediately seems critical. But should you?
Take a moment. Breathe.
Never share personal information or send money on impulse. Chances are, it’s a vishing scam.
Scammers thrive on impersonation and emotional pressure. They push you to act quickly, hoping you won’t stop to question their legitimacy.
Instead, end the call. Contact the organization directly (using a known number) to confirm the details—especially if the request was unexpected.
11. Conduct Security Awareness Training
This is arguably the most important way to stay safe online. Staying current on digital crimes gives you the knowledge needed to protect yourself, your business, and your family.
Discover how to protect business data by creating an engaging cybersecurity awareness training program using our free guide.

Learn how to implement an engaging and successful cybersecurity awareness training program.
Protecting Your Online Identity is Possible
Now that you’re equipped with the knowledge to protect your identity online, you can take action to prevent scammers from targeting you. By staying current with your training, you’ll continue to safeguard yourself even as scammers develop new, sophisticated tactics.
Remember, always be proactive. Check out our article on occupational fraud to protect your business from internal risks.










