As a small financial business, staying secure is vital to your success. Use these 9 layers of cybersecurity protection to help safeguard your data and resources.
Ever wonder why cyber thieves seem to have their eyes on small financial services firms like yours? Well, it’s time to flip the script so you can see things from their perspective. Financial services such as accounting, retirement planning, and insurance create a rich cache of personal financial information. It’s bustling with electronic money transfers and email-initiated transactions. This type of environment demands a layered approach to cybersecurity.
Unfortunately for most small- to medium-sized businesses (SMBs), securing IT infrastructures isn’t exactly in the budget.
But we’ve got a solution.
We’re diving into those layers of cybersecurity by starting with the Cybersecurity Risk Pyramid to show you how to protect your clients’ precious data without breaking the bank.
Spoiler alert: The top risks might not be what you expect.
Ready to outsmart those cyber thieves? All right! Let’s get to strategizing your cybersecurity defenses.
Rank Cybersecurity Risks from Most Likely to Occur to Least Likely
Risk pyramids are a familiar concept to those of you in the financial advisor world. For retirement planning, at the pyramid’s base are the safe “gotta-haves,” like a 401(k) and/or pension. At the top, are the more speculative “nice-to-haves,” like stocks.
Dave Jones, IT manager at Pearce, Bevill, Leesburg, Moore, P.C. in Birmingham, Alabama, provides an excellent example of a cybersecurity pyramid in action.
Dave, a 20-year financial sector IT veteran, shared his practical approach to cybersecurity in an article he wrote for CPA Practice Advisor. We asked Dave to walk us through an updated version of his Cybersecurity Risk Pyramid.
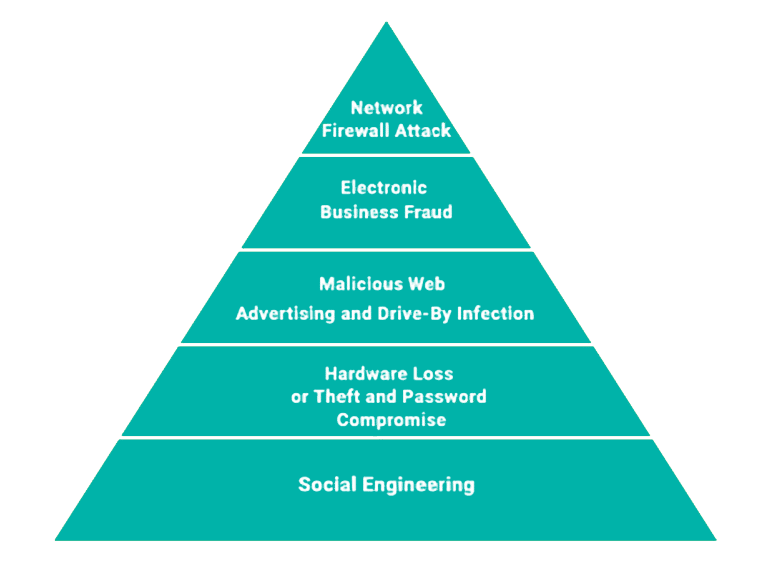
We’ll start by summarizing the five risk levels your business faces. Then, we’ll provide details on the nine interlocking strategies for addressing these risks.
LEVEL 1 (MOST COMMON) - Social Engineering
Social engineering attacks mainly result from human error – often with phishing being the culprit.
“Phishing is responsible for around 70% to 90% of all malicious data breaches, and most companies probably spend less than 5% of their budget on it,” says cybersecurity author Roger Grimes.
In addition to writing ten books, Roger has been a computer security columnist for CSO and InfoWorld magazines. He now works as a “data-driven security evangelist” for KnowBe4, an IT security awareness training company.
Roger and Dave agree that phishing emails deliver almost all ransomware and other malware. This means that phishing has graduated to more sophisticated and harmful crimes (see Level 4).
LEVEL 2 - Hardware Loss or Theft and Password Compromise
If you have employees using laptops, tablets, and phones on the road (at clients’ offices, hotels, coffee shops, etc.) some of these devices will be lost or stolen. It’s inevitable.
Weak passwords and unencrypted data on mobile devices that have weak passwords and unencrypted data can get your business into big trouble quickly, Dave says. Especially if your employees typically have clients’ sensitive financial data stored on those devices.
LEVEL 3 - Malicious Web Advertising and Drive-By Infection
You don’t have to click on infected links/attachments in emails to unleash malicious code onto your computer.
Some web pages are infected with “malvertising” or “drive-by download” coding. All you have to do is simply open a page with that coding on it with your computer or phone… and boom!
The bad code jumps on board – helping hackers find an easy way into your data, and then into all other networked devices.

According to Roger, it’s most often accomplished through popular software that hasn’t been updated regularly – so its security patches are out of date (typical targets being Adobe Flash, Java, and web browser add-ons).
“Even if a device is fully patched, threats like cryptominers can silently compromise a device by injecting JavaScript into otherwise legitimate website code,” Roger says.
“The user’s browser will automatically consume and execute that malicious code.”
Dave estimates that about 99% of your cyber threats will come from these bottom three levels. But don’t let that estimate fool you.
The remaining 1% of attacks can still easily total several per month or more. And it only takes one successful attack to do catastrophic damage.
LEVEL 4 - Electronic Business Fraud
The goal of many Level 2 phishing attacks is to identify companies that regularly transfer funds electronically, so scammers can build “spear phishing” attacks.
These are fewer (and thus on Level 4), but more sophisticated than regular phishing.
Spear phishing is a common tactic in a type of electronic fraud called business email compromise (BEC) attacks.

Trend Micro tracked 9,291 BEC attempts in 2018 Q1-Q3, a 46-percent increase from the same period in 2017. Dave says BEC attacks can slip past antivirus software because they don’t include the telltale links or attachments.
Instead, they use information available on the company’s website or on social media to dupe employees into surrendering login IDs and passwords.
With that information, scammers imitate C-suite executives to pressure employees, who normally handle wire transfers, into electronically paying into accounts controlled by the scammers.
LEVEL 5 (LEAST COMMON) - Network Firewall Attack
Not all data breaches result in theft of data.
A breach can simply be the accidental exposure of data. But the kind of breach that makes the headlines is when criminals deliberately break through a network’s defenses and harvest data.
Dave puts it atop his pyramid because, although it gets all the ink, it’s simply not as prevalent as the threats lower in the pyramid.
So, while a SMB’s cybersecurity program should protect against firewall hacks, that shouldn’t be the program’s focus.
Nine Layers of Cybersecurity Protection for Financial SMBs
We’ve combined recommendations from Dave, Roger, and Teal into nine layers of cybersecurity protection.
With all nine in place, you’re protecting against all five levels of risk shown on the pyramid. At the same time, you’re concentrating your cybersecurity resources on the most likely threats in the lower levels.
1. Employee Training
Most risks illustrated by the Cybersecurity Risk Pyramid stem, in some fashion, from human error. That makes training the most important protection of all.
Simulated phishing campaigns are critical, says Roger.
“Employers don’t think they need to simulate phishing – education is enough. But it really does take a combination of the two,” he says.
“And you need is to run these tests about once per month to get the best results.”
2. Antivirus or Endpoint Security
Loading an antivirus program on every workstation may not adequately safeguard your network from viruses anymore.
Viruses can be engineered to invade through other devices or “endpoints.” This is why small businesses often use a more advanced strategy called endpoint protection or endpoint security.
This approach centrally monitors all endpoints – including workstations, mobile devices, servers, printers, etc.
3. Application Whitelisting
Tools, such as Windows AppLocker, help you prevent software from running on your company’s computers that your IT manager or vendor hasn’t explicitly allowed.
“If you use application whitelisting and configure it properly, that knocks out so many problems right out of the gate,” Dave says.
“You don’t have to handle every piece of software that pops up and secure it, like whack-a-mole.”
4. Security Patching
When cyber thieves discover a vulnerability in commonly used software, such as Windows operating systems, that vulnerability is often broadcast throughout the cybercrime community.
Hackers prey on these vulnerabilities, so your IT staff or vendor must be vigilant about installing patches as soon as they’re released by software providers.
5. Email Virus / Spam Filtering
Standard email programs have anti-virus tools built in. However, Dave recommends external services, such as AppRiver, to stop virus- and spam-laden emails before they get to your servers.
6. Encryption
In case a virus does get through to your network, be sure your databases that store and/or backup clients’ financial information are encrypted. The data stored on workstations, laptops, and other mobile devices should also be encrypted.
As an additional protection for financial services firms, consider a policy of encrypting your emails.
7. Strong Password Policies and Multi-Factor Authentication (MFA)
Use a password manager, such as LastPass, to help employees create strong passwords that are used only for network login.
If an employee has more than one network-level password (e.g. one for an office workstation and another for a VPN), those passwords should be different.
Add another layer of security with MFA, which requires an additional login step to your password.
Example
In addition to a password, users must enter a security code sent to their cell phone or to a key fob.
8. Firewall Content Filtering
Even small firewalls now offer filtering of different categories of content. At a minimum, “advertising” and “recently registered domains” should be blocked.
9. Proven Professional Oversight and Monitoring
Even with the previous eight layers of protection in place, attacks will slip through. Guaranteed. It’s simply not possible to detect and subdue every attack a business faces today.
However, if your network is monitored by IT security experts, either on-staff or through a vendor, you have a better chance of catching anything unusual that manages to sidestep automated tools.
A dedicated security expert can also custom-design filters that, for example, identify specific language scammers may use to target your specific products, services, and employees.
Example
Dave has created an email filter for phrases that phishing scammers tend to use when targeting CPAs.
Assess Your Firm’s (or Provider’s) Cybersecurity Knowledge
Not all IT services providers are financial services cybersecurity experts. Some are more focused on basic monitoring, installations, and tech support.
That’s why SMB executives, who aren’t IT experts, must ask potential cybersecurity providers questions to determine whether they:
- Understand the current threat landscape.
- Are aware of seasonal threats and regulatory requirements that face your firm (e.g. tax-related deadlines, data retention rules).
- Stay current with security news from inside and outside of the financial services industry.
- Take responsibility for ongoing security awareness training for your employees.
One of the main barriers to small financial services businesses seeking the proper level of cybersecurity protection is that they haven’t experienced a cyber theft or breach (that they know of) yet.
Don’t wait that long. Start implementing these nine layers of cybersecurity protection now.
We provide sophisticated cybersecurity services to many small financial institutions. If you’re interested in outsourcing cybersecurity, one of our technical business advisors would be happy to see if we’re the right fit for your firm.










